In this project we will implement the technique of randomized exponentiation as a measure against side channel attacks. This approach achieves masking at the algorithmic level rather than utilising arbitrary circuits.
Systems secured by cryptographic algorithms are vulnerable to so-called side-channel attacks.
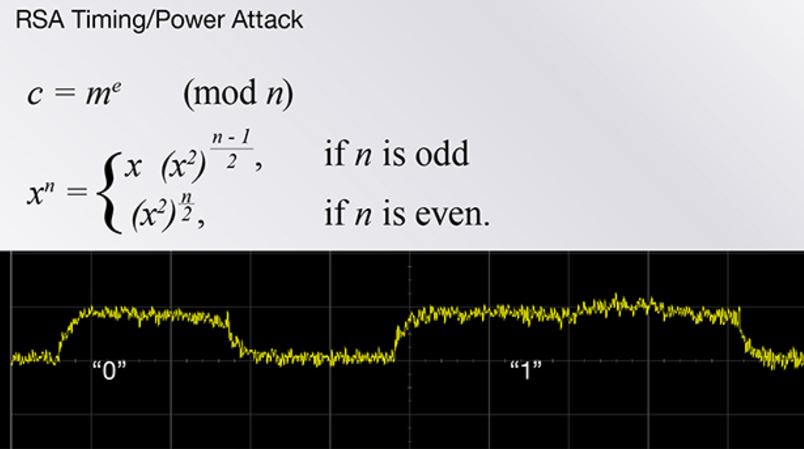
In this type of attack, an opponent attempts to discover the secret information by exploiting features of the physical implementation of the algorithm rather than breaking the algorithm itself. As a result, in order to be certified for use with the various government agencies and the military, the implementation must also be robust against this type of attack.
In particular, the implementation of the RSA cypher is based on exponentiation by a secret key; and modular reduction by a composite modulus, the factors of which are not known to an adversary. In turn exponentiation is implemented by repeated multiplications and the multiplications are typically implemented via repeated additions. Thus it is likely that the information about the secret key will leak by observing the length of the carry in these operations.
A natural approach to eliminating the leakage in this channel is information hiding and “masking and blinding”. Ideally we attempt to arrange the operations in such a way that the underlying bit patterns are not observable. Where this is not possible, we may attempt to overwhelm the attacker with noise or insert arbitrary operations to give the appearance of a uniform pattern.
Requirements:
In this project we will implement the technique of randomized exponentiation. This approach achieves masking at the algorithmic level rather than utilising arbitrary circuits.
By doing a transformation on the factors of the exponentiation (base, exponent, modulus) prior to the operation, we are in fact hiding the information. The attacker will be able to observe the bit patterns and the length of the carry chains, however these will not be relevant to the actual secret information.
By participating in this project the students will implement a robust method to prevent side-channel attacks in the RSA cipher. Tools to be used are Verilog HDL simulations, synthesis, place and route, and SPICE where necessary to analyse the power traces.
Supervisor : David Fleisher

